First off … I’ve tried configuring WireGuard multiple times (around 6 by my count) on different devices (an Ubuntu VM, a few Raspberry PIs, and a pfSense firewall) all with various versions of success. None of my attempts ended up working fully though. I would be able to access internal resources but not the internet, the internet but nothing internal, or nothing at all (by this point there would be a Raspberry Pi shaped hole in the window).
So I gave up (bad tech guy, go sit in the corner and use a Windows machine for a while).
Then, during my weekly listen of SecurityNow, Steve Gibson mentioned Tailscale as a service that uses WireGuard (episode 830) and that it’s really easy to configure. I figured, why not … let’s give it another go … and I like it!
The highlights:
- Works on Ubuntu (or any Linux distro for that matter)
- Works on Mac/iOS devices
- Works on Windows (yay … I guess?)
- Works on Android
- It’s fast
- The free tier is very generous (the paid versions aren’t bad either, especially “Subnet router failover” on the Business plan!!)
As part of my setup, I have a Raspberry Pi on my home network that acts as an exit node (so I can access Internet resources through it from anywhere) and as a gateway to my internal network. I’m getting the following speeds using Google’s speed test while sitting on a public WiFi network about 30 miles from my house.
| Without Tailscale Active | With Tailscale Active | |
| Download | 41.7 Mbps | 10.7 Mbps |
| Upload | 19.3 Mbps | 16.9 Mbps |
Those speeds aren’t exceptional, but I have residential cable (not super fast) and am using a Raspberry PI 3B+ as the gateway. All things considered, I’m happy with those speeds.
Tailscale has excellent documentation, so I’m not going to repeat it here (unless ya’ll want me to, in that case, leave a few comments to that effect). The one thing I wasn’t able to find in their docs was why my Ubuntu machine wasn’t getting routed to my internal home network, even though the exit node worked perfectly. The secret sauce is to run the following command on your Ubuntu machine (telling it to actually use the routes that you’ve configured as available on other devices):
sudo tailscale up --accept-routesOh, that brings up another point. The Ubuntu client is not graphical, but command line only (and everyone rejoices, since command line is the only way to use stuff … right?!).
One downside of using Tailscale versus pure WireGuard is that it does depend on Tailscale’s servers remaining up (er, not true … bad blog writer, see my update below). To mitigate against being locked out of my network I would setup a monitor on my Tailscale machine, if it detects that the Tailscale network is down, it could bring up a WireGuard instance or L2TP over IPSEC (I know, those are dirty words … going to go wash my keyboard with organic vegan battery acid) server. If you’re interested in a write up of how to implement a system like that, leave a comment, if there are enough people with interest (let’s say [number of comments with interest] / [total number of comments] * 100 > 50) then I’ll do it.
2021.09.07 Update: Ross Zurowski (https://twitter.com/rosszurowski) let me know that my previous paragraph about Tailscale’s servers needing to remain online is not accurate (I always appreciate this kind of feedback, thank you!), by noting that:
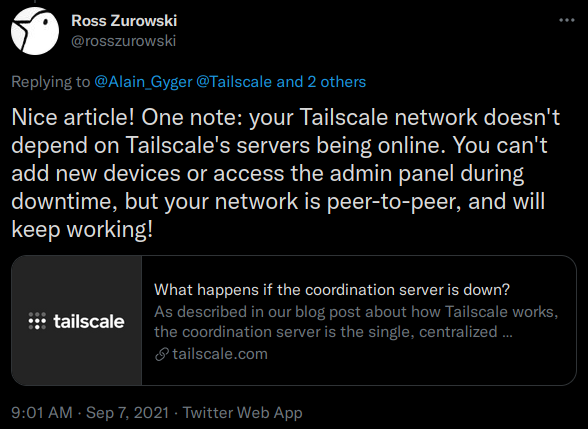
The link points to a FAQ on Tailscale’s website: https://tailscale.com/kb/1091/what-happens-if-the-coordination-server-is-down/ (sounds like something I’d like to test by blocking traffic to Tailscale’s coordination server and seeing what happens …)
I suggest (for whatever that’s worth) you give Tailscale a try.